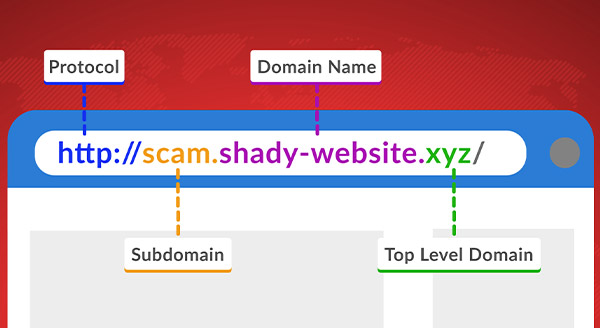
Do You Really Need It All? Understanding the Need for Comprehensive Cybersecurity
As a business owner, your top priority is keeping costs low while still supporting growth. When your managed service provider recommends investing in a robust stack of cybersecurity software, it's…